Operational Technology
Operational Technology Cybersecurity Solutions
VCSPro delivers the strategic, unified approach essential for securing today's complex operational environments through effective Information Technology and Operational Technology, known as IT/OT convergence. Our certified consultants navigate the complexities of integrating data focused IT with physical process-oriented OT, offering a comprehensive solution that covers both technological and organizational aspects. We guide you through the intricacies of physical, software and organizational convergence, actively aligning these traditionally separate worlds to enhance efficiency, innovation and resilience. We acknowledge that OT systems require specialized security beyond traditional IT measures.
How We Help Your Organization
- Navigate the Convergence Landscape: We guide you through the complexities of physical, software, and organizational convergence, ensuring a tailored approach that aligns with your specific needs and goals.
- Foster IT/OT Alignment: We facilitate collaboration and communication between IT and OT teams, ensuring that security strategies are aligned with operational realities.
- Conduct Holistic Risk Assessments: We conduct thorough evaluations that encompass both IT and OT systems, identifying vulnerabilities and potential attack vectors in the converged environment.
- Develop Tailored Security Solutions: We design customized security solutions that address the specific needs of your IT/OT environment, taking into account factors such as legacy systems, real-time data requirements, operational constraints, and the increasing use of IoT devices.


Take control of your cybersecurity today—start with our free self-assessment!
The Cybersecurity Triad and How It Integrates Between OT and IT
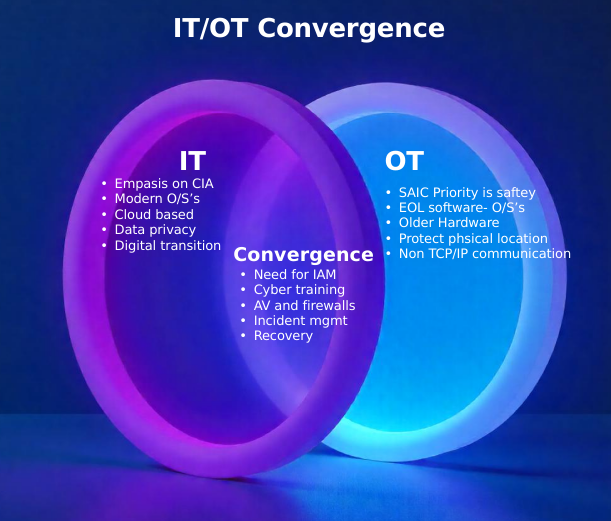
Although both Information Technology (IT) and Operational Technology (OT) environments face growing cyber risks, their fundamental cybersecurity priorities differ significantly when considering the core principles of the Security Triad: Confidentiality, Integrity, and Availability (CIA). In IT, the typical priority order often places Confidentiality (protecting information from unauthorized access) at the forefront, followed by Integrity (ensuring data accuracy and preventing unauthorized modification), and then Availability (guaranteeing timely and reliable access to resources).
In contrast, the OT domain typically reverses this order and places the utmost importance on Safety as the primary concern. This leads to a Safety, Availability, Integrity, Confidentiality (SAIC) model for OT. Here, Availability (ensuring continuous operation of critical industrial processes) takes precedence after safety, followed by Integrity (maintaining the correct functioning of industrial controls), and finally Confidentiality (protecting sensitive operational data). This shift in focus reflects the critical need to protect human lives and ensure continuous industrial operations, as compromised OT systems can have direct physical consequences, unlike many IT breaches.

Information Technology (IT) - CIA
Operational Technology (OT) - SAIC

Convergence of IT and OT in a digital world
IT vs. OT Priorities: IT security prioritizes CIA, while OT security emphasizes SAIC due to potential real world impacts.
Need for Harmonized Security: As IT and OT systems converge, a unified security approach is essential to protect both digital assets and physical operations.
Collaboration for Resilience: Effective cybersecurity requires collaboration and knowledge sharing between IT and OT teams to ensure comprehensive protection and operational resilience.

Harmonizing OT and IT
Expertise in IT/OT Integration: VCSPro understands the unique challenges and complexities of integrating IT and OT systems.
Holistic Security Strategy: We develop unified security strategies that treat IT and OT as interconnected parts of a single industrial environment, not as separate entities.
Comprehensive Risk Management: By analyzing inter dependencies, we identify vulnerabilities and implement security controls that protect your entire IT/OT ecosystem.
Take control of your cybersecurity today—start with our free self-assessment!
